Authors:
(1) Amit Seal Ami, Computer Science Department, William & Mary Williamsburg, Virginia, USA, and this author contributed equally to this paper (aami@wm.edu);
(2) Syed Yusuf Ahmed, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper (bsse1013@iit.du.ac.bd);
(3) Radowan Mahmud Redoy, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper (bsse1002@iit.du.ac.bd);
(4) Nathan Cooper, Computer Science Department, William & Mary Williamsburg, Virginia, USA (nacooper01@wm.edu);
(5) Kaushal Kafle, Computer Science Department, William & Mary Williamsburg, Virginia, USA (kkafle@wm.edu);
(6) Kevin Moran, Department of Computer Science, University of Central Florida Orlando, Florida, USA (kpmoran@ucf.edu);
(7) Denys Poshyvanyk, Computer Science Department, William & Mary Williamsburg, Virginia, USA (denys@cs.wm.edu);
(8) Adwait Nadkarni, Computer Science Department, William & Mary Williamsburg, Virginia, USA (apnadkarni@wm.edu).
Table of Links
6 Future Work and Conclusion, Acknowledgments, and References
5 USING MASC
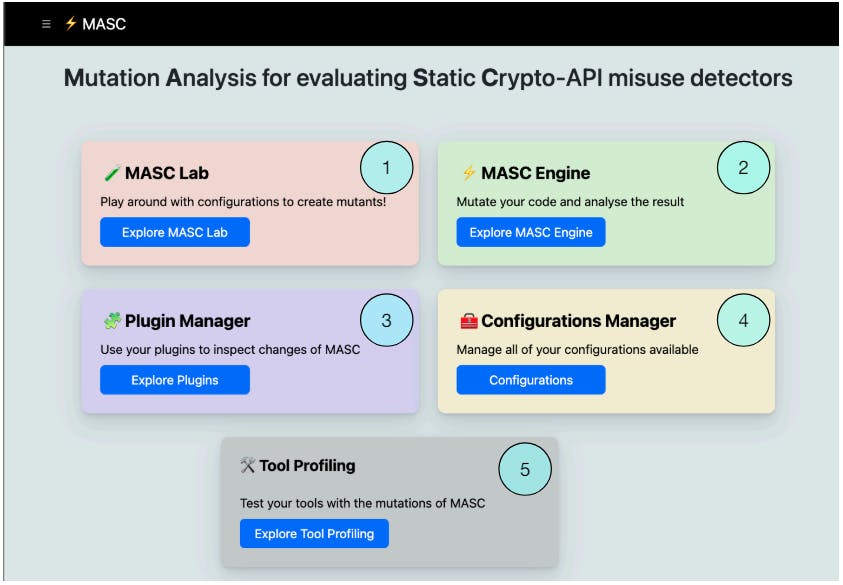
As described previously, MASC has both command line interface and web-based front-end (MASC Web, shown in Figure 3). MASC CLI can be executed by providing a configuration file e.g., Cipher.properties using the command shown in Listing 4. Similarly, using the MASC Web, users can do the following, labeled as per Figure 3:
(1) Experiment and learn about crypto-API misuse using MASC Lab,
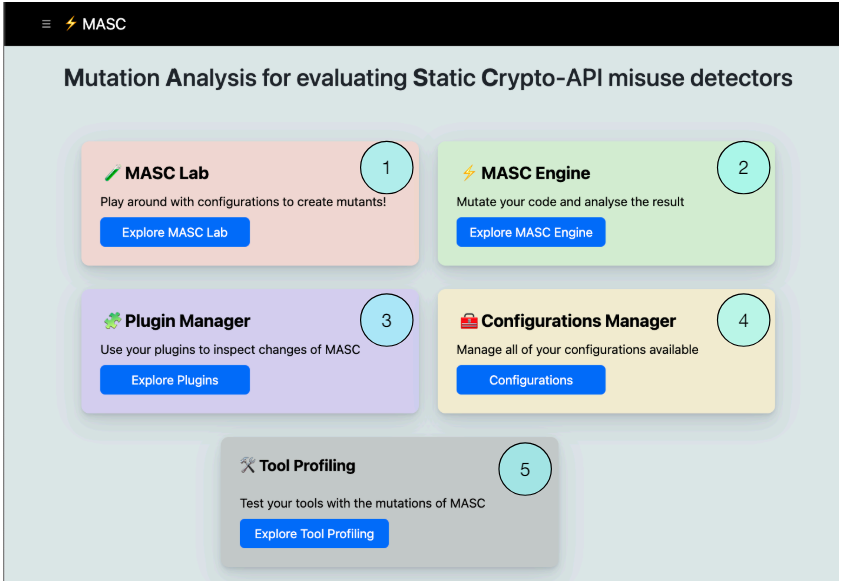
(2) Mutate open source applications by uploading the zipped source code in MASC Engine,
(3) Use custom implemented mutation operators as plugins,
(4) Create and upload configuration files, and
(5) Profile crypto-detectors by analyzing caught and uncaught mutants.
The detailed description of each of these, with example configuration files, and detailed developer documentation, is shared in the open-source repository of MASC [2].
This paper is available on arxiv under CC BY-NC-SA 4.0 DEED license.